B-Cryptoband
A wearable Security Authentication System


B-Cryptoband is a wereable device for business that provides functionality to authenticate as a PIV-compliant smart card out-of-the-box. It can work with several OS (Microsoft Windows Server 2008 R2 and later servers, and Microsoft Windows 7) and it is compatible with Linux and macOS operating systems with the OpenSC software installed, for public key authentication with OpenSSH through PKCS11.
The primary goal of the B-Cryptoband is to replace smartcards as high-assurance authentication devices. B-Cryptoband can be used for two-factor authentication.
Sensitive crypto materials is handled by a Common Criteria (CC) EAL 5+ certified Secure Element (SE) chip.
It combines strong security of smartcards with the flexibility and easy of use of a wearable device
Technology
The B-Cryptoband uses a Secure-by-design approach adopted for all the architectural levels, and for the communication protocol, software and firmware.
For private key storage, secure boot and crypto acceleration the device uses HSM.
Different execution domains (BluetoothLE stack, crypto stuff and application) are separated through a micro-hypervisor. Firmware and software update are secured, always signed and verified.
On PC side, the system uses TPM when available for storing secure pairing private keys.
It is identified as a Microsoft USB CCID smart card reader and NIST SP 800-73 PIV smart card using the base Microsoft driver.
PIV is an open standard widely used in commercial and government organizations for two-factor authentication, digital signing, and encryption.
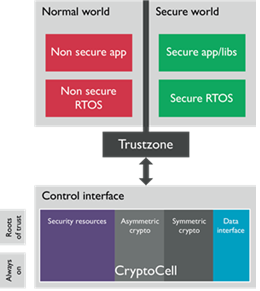
Security
B-Cryptoband has been designed thinking also from an attacker’s perspective.
It has been designed to be immune to some remote cyber-attacks for the communication channels such as passive sniffing of Bluetooth Low Energy (BLE) traffic,
Man-In-The-Middle (MITM),
Replay/relay attack against NFC and Bluetooth Low Energy (BLE)
We have applied advanced anti-tampering techniques for all software modules developed on Windows of both user-space and kernel-space.
In particular we have developed protection from SW analysis by Reverse Engineering and protection from run-time code injection attack by malwares
.
Hardware Specs
- Secure CPU (1MB flash, 256KB ram, external SPI flash up to 256MB)
- Bluetooth Low Energy
- Display
- Vibration
- Heart rate sensor
- NFC
- Accelerometer
- 105mAh Li-Po battery

Use Cases: Enterprise Company Scenario
The B-Cryptoband can be used unlimited use cases such as convenient 2-factor authentication, smart card LogOn, distance auto log-off, mail and data encryption, etc… With it we can ensure user identity and improve security policies. Moreover, it is possible to use it with several different devices at the same time and guarantee a strong authentication with all of them.
Here we show up some of the most common usage of our device in different working situations.
Smartcard replacement
- PKI logon into their workstations
- Digital Signature
- Data Encryption (email/file)
- Support for multiple identities


Factory 4.0
- Enable tools and keep track of their usage (e.g., at the assembly line, in a lab, etc)
- Hands-free: can be used without un-wearing glows
- Save time respect to traditional systems (smartcards, paper tickets, …)
- Alerts when it is time to rest and display the remaining time
Everyday office life
It can replaces access, identity and payment badges.
- Keep track of employees clock in/clock out
- Physical access and access control/supervision(buildings, special areas or rooms, garage)
- Enable/disable user identity (Microsoft ActiveDirectory and building doors opening) during the service hours
- Payment solutions (canteen, vending machines, printers)

In case you need technical integration or consultancy services, our partners will be more than happy to assist you.
